7 Simple Techniques For Spam
Wiki Article
Getting The Spam To Work
Table of Contents5 Simple Techniques For Spam8 Easy Facts About Spam Described

destructive code. Now, if somebody is looking for' where to purchase Molly', he would certainly locate the injected web site ABC in addition to the search results page. If that site visitor clicked that search results page, he would directly reach the Cialis payment entrance. This site visitor would certainly never ever arrive at ABC. In this situation, the evil website XYZ has ended up being a bloodsucker living off the credibility of the.
non-suspecting ABC. At this point, you should ask these two concerns; Why was my internet site targeted for the SEO spam attack? Exactly how did the attacker procure within and also install his web content? Hackers don't target individual sites; they browse for numerous internet sites at one go and afterwards locate the most convenient targets. According to a record, 36 %of all Word, Press-based websites use outdated versions of this CMS platform. Sites that use outdated versions are most likely to be hacked than those who have ready and up-to-date versions of WP. While WP on a regular basis goes on making its system a lot more safe, it depends on the web site proprietors to accept those modifications. Themes and plugins are terrific for performance, but in some cases, they may cause trouble for you. Frequently, we install plugins that haven't been examined by customers or, we utilize those products which don't have correct protection actions in position. Some individuals choose to install pirated plugins and also styles to save on money. Avoid making use of simple as well as common passwords such as 123456, Querty, etc. Greater than 23 million people make use of 123456 as their password, as well as that makes this one of one of the most prone and pointless tricks to a lock - Spam. In all these three instances provided above, our website comes to be susceptible to Recommended Site SEO spam. To place it simply, a backdoor is specifically what it seems like. It is an entry factor used to obtain access to your website by cyberpunks as and also when they want. These are advanced devices that scan all your collections, databases, folders, etc for infections as well as search engine optimization spams. Not all scanners can do their task well, so you will certainly have to locate the ideal ones, such as the following. Astra is a relied on name when it comes to search engine optimization spam elimination. Spam. Safety and security specialists at Astra scan your imp source internet site to reveal all.
More About Spam
web pages, posts, as well as various other locations containing malicious links. They clean up those web links and also re-submit them to Google. In case, your site was blacklisted as a result of SEO spam, Astra looks after that as well. Post all this, the Astra firewall program is installed on your site for future security against such attacks. Spam. Your site is among the most essential financial investments that you have actually made.
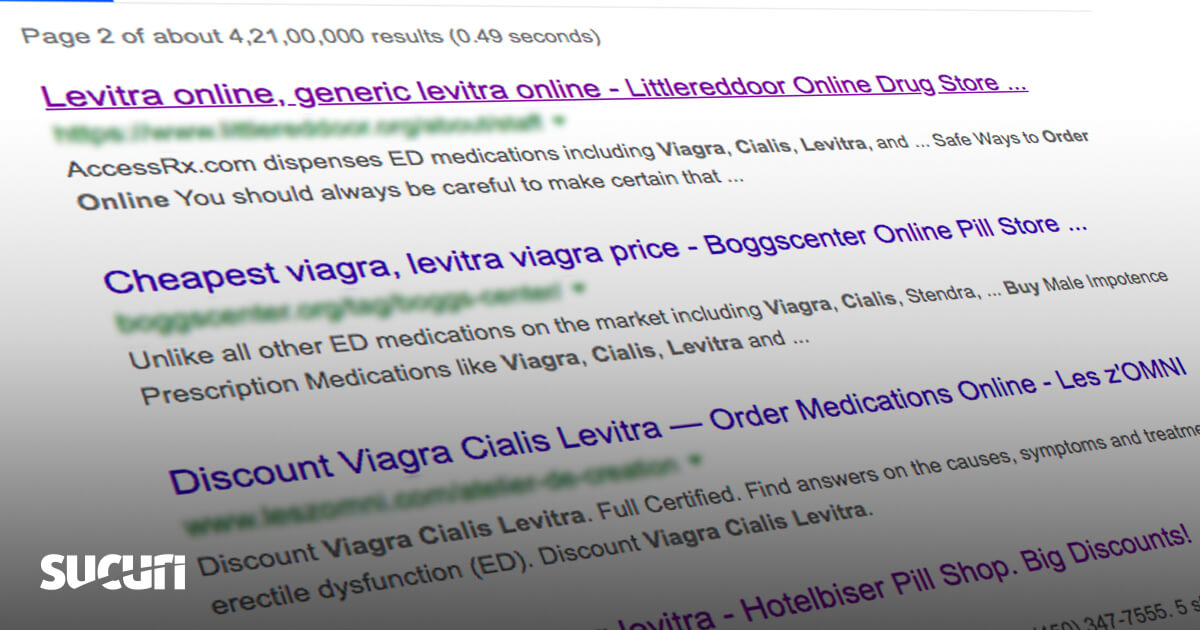
If you aren't cautious, it can be subjected to SEO spam attacks that will take away your hard-earned traffic, reputation, and also cash. Comprehending exactly how internet search engine spam functions is the very first step towards protecting on your own versus it. Right here are some of the black hat tactics that fall under the category of SEO spam : This is when assailants modify your web content to include new keywords. Generally, those key phrases will show up in high quantities, because the culprits will not appreciate how that could impact your content's readability. This is when your web site is made use of to show ads for services or products that are possessed by the spammers. These ads might have little.
to do with your site's content as well as will harm your reliability. Overall, search engine optimization spam usually isn't refined. Instead of including a couple of links or keywords, enemies will attempt to obtain the most gain from your site prior to you notice what's occurring. If you have an open comments section, you'll likely run right into spam on a practically day-to-day basis. Every website is a prospective target for SEO spam, however if you fall short to put the appropriate actions in place, you run a greater threat of becoming a sufferer. There are a great deal of ways assaulters could access to your internet site. This might be much more tough to determine if you have multiple team participants with editing consents, however when these keywords and links are unassociated to your common content, it's easy to find them. If you come throughout a web page or blog post on your internet site that you or you could try these out your teammates didn't established, that can be a clear sign of a SEO assault. You can utilize devices like Google Analytics coupled with Google Look Console to see if these drops have anything to do with safety and security problems. You may have run throughout the periodic web site that shows a protection caution when you attempt to.
Report this wiki page